Real-World Consequences:
Dr. Jake Baker's Story
In the blink of an eye, my business was hollowed out by an insider cyber attack, leading to a staggering $5 million loss and the irreplaceable theft of sensitive intellectual property. This wasn’t just a breach; it was a brutal awakening to the realities of cyber threats in the modern small business landscape. Our lack of robust cybersecurity measures left us exposed and ultimately defenseless against those we trusted. From this pivotal moment, I learned the hard way that proactive cybersecurity isn't optional—it's fundamental.

Dr. Jake Baker
Mid-Market (51-1000 employees
Meet Your Cyber Guardian –
Dianne Beattie
Brief Introduction & Mission Statement
In an era where digital threats are evolving daily, Cyber Secure Online (CSO) stands as your vigilant protector. Founded by Dianne Beattie, a seasoned cybersecurity expert with a rich heritage from the US Navy to pioneering roles at Bank of America and Chase Manhattan, CSO was launched in 2008 with a singular mission—to equip small businesses with enterprise-grade cybersecurity. Our journey is more than just offering tools; it's about making top-tier digital security accessible, understandable, and affordable for businesses poised for growth but vulnerable to cyber dangers.

What You Will Learn
The Seven Hazards Lurking in Your Digital Shadows
1. The Invisible Doorways: discover that minor oversights open floodgates
2. The Trap of Innocuous Links: the peril of phishing attacks
3. The Inside Job: the risk of insider threats
4. The Remote Work Vulnerability: the increased risks
5. The Silent Data Breach: the often-unnoticed speed and stealth of loss
6. The False Security of Obscurity: debunk the myth
7. The Cumulative Cost of Complacency: risks over time
The Invisible Doorways
Seemingly minor oversights in digital hygiene can
open floodgates for cyber predators.
Lack of awareness about who accesses your cloud environment and when can significantly increase your vulnerability to attacks.
Furthermore, the inability to guarantee that devices are utilizing a secure network when transmitting sensitive information compounds this risk.
Additionally, unprotected email inboxes represent one of today's most widespread and severe security threats, serving as a prime target for cyber attackers.

The Trap of Innocuous Links
The peril of phishing attacks and CSO's vigilant monitoring safeguards against deceptive threats
Phishing attacks pose a severe threat by potentially leading to ransomware
deployment, which can disrupt or even permanently halt business operations.
CSO offers robust protection against such risks by blocking malware introduced
through phishing attempts.
Utilizing CSO’s DNS Filtration and Secure
Web Gateway, links that could direct
clients to malicious sites harboring malware
are effectively intercepted and blocked,
safeguarding the integrity of the business's
digital environment.
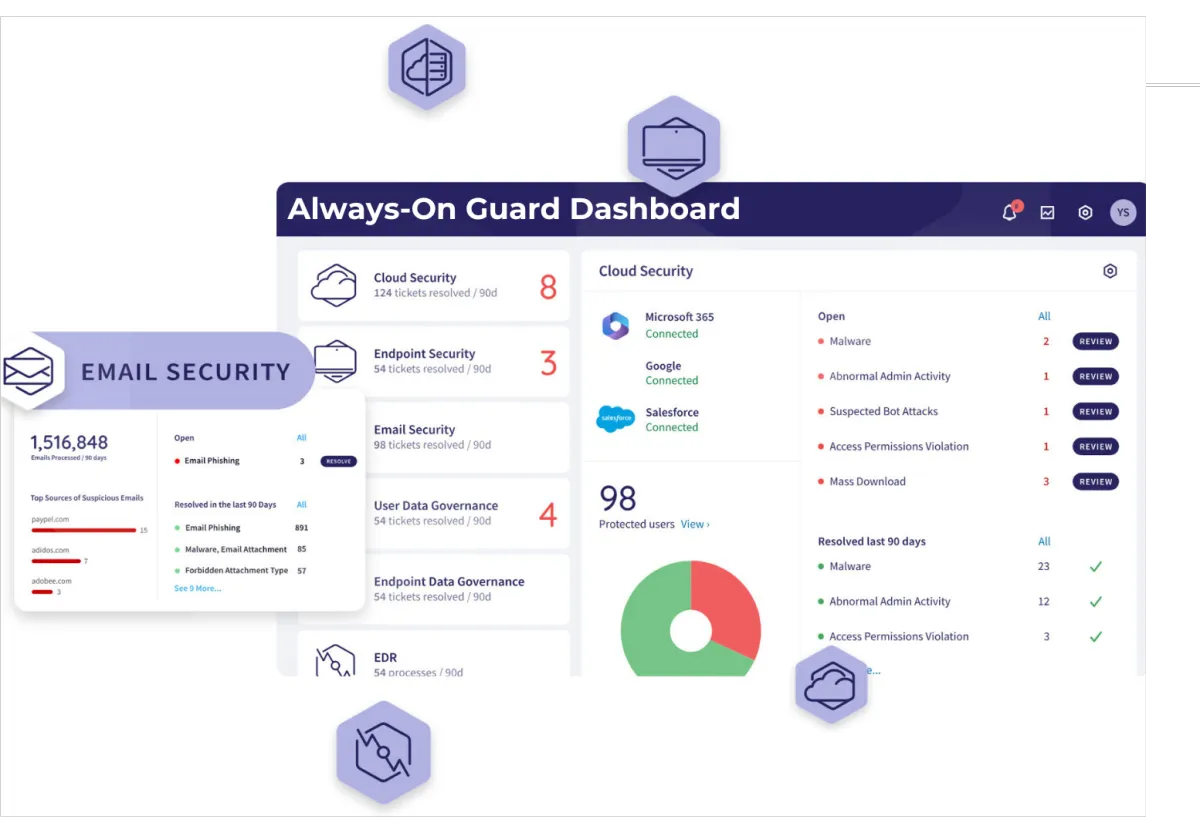
The Inside Job
Talk about the risk of insider threats and how CSO’s comprehensive user
governance tools can create a secure operational framework.
Inside job attacks can be identified and countered by our
advanced AI and machine learning technologies, which
meticulously analyze user behavior patterns, modifications
in access permissions, changes to registry keys, and the use
of legitimate credentials from suspicious IP addresses.
Our Endpoint Detection and Response (EDR) system is adept
at not only detecting these threats but also actively
remediating them, thereby providing a robust defense
against internal security breaches.

Customer Spotlight: Real Results with CSO
The Power of Instant Protection

“Integrating Cyber Secure Online into our Office 365 was seamless and swift. The admin dashboard is intuitive—no deep cybersecurity knowledge needed. Its insights directly improved our DLP training, and its remote management tools are a game-changer for us. Quarterly check-ins with Cyber Secure Online
keep us at the cutting edge.”
Jeff V., Director of IT
Mid-Market (51-1000 employees


The Remote Work Vulnerability
Remote workers sometimes overlook crucial security practices such as using robust passwords, regularly updating them, avoiding the use of unauthorized USB devices, and leaving their screens exposed in public places.
Additionally, they may inadvertently send sensitive data over insecure public WiFi networks, mistaking them for secure connections. CSO addresses these common oversights by implementing comprehensive security measures that safeguard against these vulnerabilities.
Our solutions ensure strong password enforcement, restrict unauthorized device usage, protect data even in public settings, and secure information sent over WiFi, effectively eliminating these risks for remote workers.

The Silent Data Breach
The often-unnoticed speed and stealth of data
breaches, emphasizing CSO’s proactive defenses.
CSO is equipped to identify and address security
vulnerabilities by monitoring for significant data
movements, deletions, and unusual login activities or timings.
This capability enables us to quickly respond to potential threats, safeguarding businesses from unauthorized access and data breaches.
Through vigilant surveillance and timely intervention, CSO helps mitigate the risks posed by these activities, ensuring your business's digital assets remain secure.

The False Security of Obscurity
Small businesses saw a 424% increase in cyberattacks last year
Small businesses are increasingly targeted by cyber attackers due to their connections to larger companies.
These smaller entities might have access to their larger partners’ vendor portals for billing purposes, presenting a less fortified entry point for hackers aiming at bigger targets.
This vulnerability was starkly demonstrated in the incidents involving numerous car dealerships this year, all linked by their use of a single, small-scale software developer.
The breach showed that unprotected small businesses can inadvertently become gateways to more substantial and secured networks, emphasizing the need for robust cybersecurity measures across all business sizes.

The Cumulative Cost of Complacency:
A Price Too High
We defend against attacks from all directions using a unified
approach.
Our single agent provides comprehensive visibility, eliminating
the uncertainty and delays of relying on multiple tools to
communicate vital information. This method ensures a singular
source of truth.
By effectively blocking email threats, stopping malicious websites in their tracks, preventing malware downloads, and offering the ability to halt processes and isolate devices for secure troubleshooting, we significantly reduce the chances of user error.
Our strategy offers layered protection far beyond what standard
tools can provide.

A Trustworthy Partner for Your Cybersecurity
Thank you for considering Cyber Secure Online
14-Day GROW Experience: Dive into CSO's cybersecurity impact with a no-cost, 14-day trial. Experience firsthand how we safeguard your business.
Ready to Enhance Your Cybersecurity?: Let's talk! Schedule a call to discuss how joining the CSO family can fortify your business against cyber threats today and
tomorrow.
Our mission is to equip small businesses like yours with industry-leading cybersecurity solutions, ensuring your growth is unhindered by digital threats.

CrowdStrike vs Always-On Guard
Transition from Risk to Command with The Ultimate Cyber Protection Comparison

Unseen Doorways Await... Hackers Know Them. Do You?
Let’s Secure Your Business.

Social Media Management
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
