Real-World Consequences:
Dr. Jake Baker's Story
In the blink of an eye, my business was hollowed out by an insider cyber attack, leading to a staggering $5 million loss and the irreplaceable theft of sensitive intellectual property. This wasn’t just a breach; it was a brutal awakening to the realities of cyber threats in the modern small business landscape. Our lack of robust cybersecurity measures left us exposed and ultimately defenseless against those we trusted. From this pivotal moment, I learned the hard way that proactive cybersecurity isn't optional—it's fundamental.

Dr. Jake Baker
Mid-Market (51-1000 employees
Meet Your Cyber Guardian –
Dianne Beattie
Brief Introduction & Mission Statement
In an era where digital threats are evolving daily, Cyber Secure Online (CSO) stands as your vigilant protector. Founded by Dianne Beattie, a seasoned cybersecurity expert with a rich heritage from the US Navy to pioneering roles at Bank of America and Chase Manhattan, CSO was launched in 2008 with a singular mission—to equip small businesses with enterprise-grade cybersecurity. Our journey is more than just offering tools; it's about making top-tier digital security accessible, understandable, and affordable for businesses poised for growth but vulnerable to cyber dangers.

What You Will Learn
The Seven Hazards Lurking in Your Digital Shadows
1. The Invisible Doorways: discover that minor oversights open floodgates
2. The Trap of Innocuous Links: the peril of phishing attacks
3. The Inside Job: the risk of insider threats
4. The Remote Work Vulnerability: the increased risks
5. The Silent Data Breach: the often-unnoticed speed and stealth of loss
6. The False Security of Obscurity: debunk the myth
7. The Cumulative Cost of Complacency: risks over time
The Invisible Doorways
Seemingly minor oversights in digital hygiene can open floodgates for cyber predators.
Problem: Think of your business like a house with doors you didn't know were unlocked.
These "hidden doors" could be: a Wi-Fi network that's not secure an employee clicking on a bad link easy-to-guess passwords.
These weak spots are exactly where hackers can get into your business.

CSO's Solution: CSO is like your home security system.
We make sure your Wi-Fi is locked tight, teach your team how to spot sneaky tricks from hackers, and set up stronger locks (passwords and extra checks) so only the right people can
get in.
Hackers look for easy ways into your business. CSO finds and locks up these weak points, keeping your business safe.
The Trap of Innocuous Links
The peril of phishing attacks and CSO's vigilant monitoring safeguards against deceptive threats
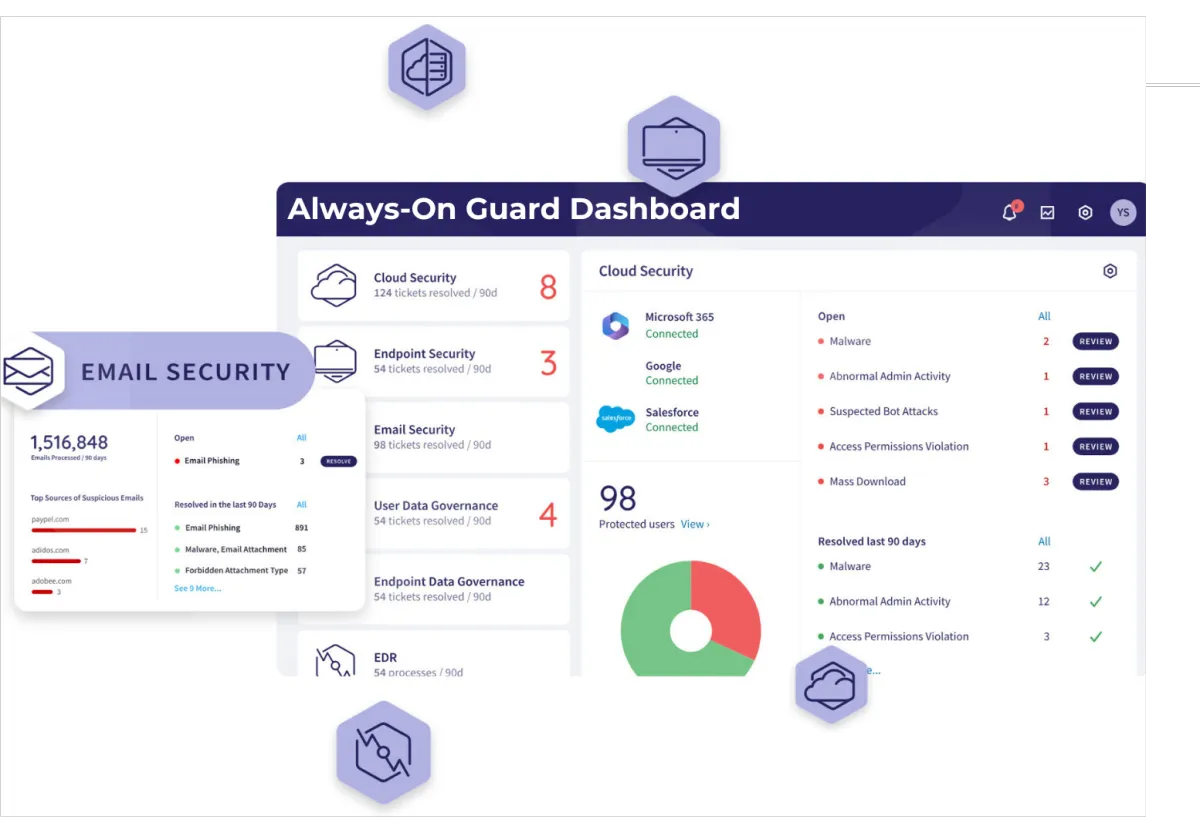
The Always-On Guard Dashboard is engineered as the central nervous system with advanced protection tailored for small business operations.
Always-On Guard Dashboard
Stand out with exclusive features like WiFi Phishing prevention, User Governance and Inbound Email Gateway protections.
The Inside Job
Protecting Against Insider Threats
Guarding Against Insider Threats
¤ Stop Data Leaks: Proactive protection keeps your information safe.
¤ Smooth Operations: Cybersecurity that keeps your business running without interruptions.
¤ Easy Compliance: Navigate regulations with ease, staying focused on your work.
¤ Build Trust: Show customers their data is secure; enhance their
confidence in you.
¤ Grow Safely: Our security scales with you, protecting you as you expand.
CSO’s Advantage: Comprehensive tools target precisely who has access, making your network secure from the inside out.

The Power of Instant Protection

“Integrating Cyber Secure Online into our Office 365 was seamless and swift. The admin dashboard is intuitive—no deep cybersecurity knowledge needed. Its insights directly improved our DLP training, and its remote management tools are a game-changer for us. Quarterly check-ins with Cyber Secure Online
keep us at the cutting edge.”
Jeff V., Director of IT
Mid-Market (51-1000 employees


The Remote Work Vulnerability
Security Beyond the Office
¤ Anywhere Protection: Secure remote work environments as if you're in the office.
¤ Zero Disruptions: Maintain productivity with seamless cyber defense for remote teams.
¤ Access Control: Ensure only the right people can access your data, anywhere, anytime.
¤ Secure Connections: VPN and encryption for safe data transmission, no matter the location.
¤ Future-Proof: Adapt to the evolving work landscape with flexible, robust security measures.

CSO’s Strategy: Tailored security that moves with your team. From home offices to coffee shops, we've got you covered.
The Silent Data Breach
Stealthy Threats, Vigilant Defense
¤ Immediate Detection: Spot breaches the moment they occur, stopping hackers in their tracks.
¤ Continuous Monitoring: 24/7 surveillance ensures no threat goes unnoticed.
¤ Rapid Response: Swift action to neutralize threats, minimizing potential damage.
¤ Data Recovery Plans: Prepare for the worst with strategies to recover lost data quickly.
¤ Peace of Mind: Knowing your business is monitored round the clock brings unparalleled calm.

CSO's Response: Before they whisper, we're already there. CSO's preemptive measures mean you're protected from breaches you never knew existed
The False Security of Obscurity
Small businesses saw a 424% increase in cyberattacks last year
¤ Universal Target: Small businesses are just as at risk as the big names.
¤ Myth Bust: Obscurity doesn't equal safety. Hackers exploit any vulnerability.
¤ Real Risk Assessment: Understand where you're vulnerable, no matter your size.
¤ Tailored Defense: Security solutions adapted to fit the unique needs of your business.
¤ Awareness and Action: Educating your team on risks and defenses strengthens your security posture.1 Column

CSO's Insight: Every business stands out to a hacker. CSO ensures you're armed and invisible to cyber threats, debunking the myth that small means unnoticed.
The Cumulative Cost of Complacency:
A Price Too High
¤ Rising Risks: Every ignored threat multiplies, increasing your vulnerability.
¤ Long-term Impact: Delayed action can lead to irreversible damage to reputation and finances.
¤ Proactive Pays Off: Investing in cybersecurity now saves costly consequences later.
¤ Security as Investment: View cybersecurity not as an expense, but as critical investment in your business's future.
¤ Partner in Protection: CSO is your ally, helping you stay ahead and secure.

CSO’s Commitment: Don’t wait for a breach to realize the value of security. With CSO,
you’re not just protected today—you’re preparing for tomorrow.
A Trustworthy Partner for Your Cybersecurity
Thank you for considering Cyber Secure Online
14-Day GROW Experience: Dive into CSO's cybersecurity impact with a no-cost, 14-day trial. Experience firsthand how we safeguard your business.
Ready to Enhance Your Cybersecurity?: Let's talk! Schedule a call to discuss how joining the CSO family can fortify your business against cyber threats today and
tomorrow.
Our mission is to equip small businesses like yours with industry-leading cybersecurity solutions, ensuring your growth is unhindered by digital threats.

CrowdStrike vs Always-On Guard
Transition from Risk to Command with The Ultimate Cyber Protection Comparison

Unseen Doorways Await... Hackers Know Them. Do You?
Let’s Secure Your Business.

Social Media Management
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.

