How to Protect Your Business from Phishing Scams
How can I be sure my business is protected from scams and phishing emails without hiring a full IT team?

How can I be sure my business is protected from scams and phishing emails without hiring a full IT team?

Cybersecurity has evolved far beyond its roots as a purely technical or IT concern. Today, it is a core pillar of customer trust, brand reputation, and business success.
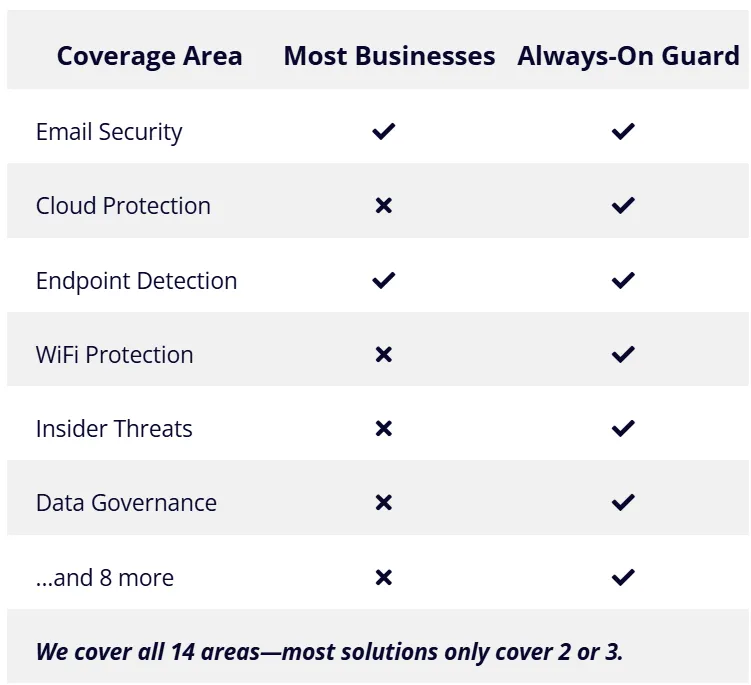
Always-On Guard vs CrowdStrike Comparison

In an era where cyber threats loom larger than ever, Cyber Secure Online stands as a beacon of hope and resilience. From cybercriminals to hostile nation-states, our enemies are relentless in their attacks on our way of life. They target our businesses, critical infrastructures, and even our unity with disinformation campaigns. This video dives deep into the pervasive cyber threats that seek to undermine our society and highlights the urgent need for comprehensive cybersecurity measures. Learn how Cyber Secure Online can arm businesses and organizations of all sizes with the tools to establish robust defenses, counter ransomware attacks effectively, and ensure quick recovery from breaches. Discover the importance of assessing your security controls and identifying gaps through Third-Party Vulnerability Assessments to stay a step ahead of adversaries. Together, we can secure the blessings of liberty for our generation and those to come. Join us in fortifying our digital fortresses and safeguard our connected world. https://cybersecureonline.com