1-888-988-5567
"DataSafe" Policy Pro Enforcer | Reduces Human Risk
Welcome to a new era of cybersecurity compliance, training and governance
Discover tailored cybersecurity measures crucial for robust organizational resilience against digital threats.
Human Error = 75% of data breaches
Password reuse happens with 44% of people
43% of people made a mistake with serious cyber security consequences
20-30% of untrained users will FAIL basic phishing test
Cybercrime will cost $10.5 trillion annually by next year
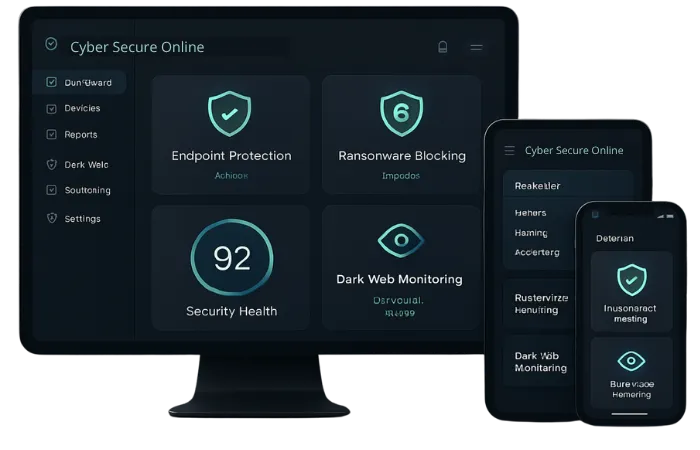
Track, Train, and Amplify Compliance
Transform your small business from a hacker’s target into an impenetrable fortress.
Tailor-Made Security Just a Smile Away: Select Your Custom
Training and Compliance Enhancements – Explore Now!
Navigating the digital world’s choppy waters requires more than just a good antivirus – it’s about having an entire armory at your disposal. At Cyber Secure Online, we equip you with cutting-edge cybersecurity solutions, curated to snugly fit your business’s needs while meeting (and often sailing past) industry compliance standards. Uncover our treasure trove of ADD-ONs designed to bolster your defenses, wise up your team, and smooth out those compliance wrinkles. And remember, we're all about flexibility and custom-fit solutions – a little kindness goes a long way, and it might just unlock the perfect bundle tailored just for you."
Click the buttons above to learn more and read success story profiles....
DataSafe Policy Pro Enforcer
Policy Driven Awareness & Gamification Training (Add-On)

Boost your business's security the smart way with our Symbol Policy Management system. We'll show you how to make those must-do compliance rules work for you, turning them into a powerhouse defense against cyber threats. Our system is a breeze to customize, fitting just right with what your business needs, plus it comes packed with easy-to-follow lessons on all the big cybersecurity topics. Effective governance is not just crucial; it's indispensable to track, train and amplify compliance.
With just a few clicks, you can also test your team with real Email Phishing challenges and get everything you need to show you're following the rules, all in one place. It's total protection made simple, designed for any business, big or small.
This base monthly plan begins at $99/mo includes one user and scales from there. Additional users can be added as needed.
Policy Creation & Modification
Start with adaptable policy templates that align with your organization’s unique needs.
Our intuitive editor allows for seamless modifications, ensuring your policies remain up-to-date and relevant.
Transform complex policy development into a straightforward task.
Users Trained on Policies
CSO's extensive training library with your policy distribution strategy will educate employees comprehensively to mimic real-life phishing attacks or security breaches tailored to your policies.
Our centralized training and compliance repository is designed with governance at the core, ensuring transition from awareness to action is seamless.
Policy Distribution & Signature
Managing the process of Policy sign-off is simple with e-signature, tracking, and auto-reminders. We remove the traditionally cumbersome nature of ensuring company-wide sign-off.
Monitor policy engagement and compliance in real time, allowing for targeted follow-ups and ensuring no employee is left behind.
Policy Driven Cyber Awareness Training
Boost your computer security and meet important rules easily by using a proven checklist. It helps you check everything’s safe, just like a security guard for your computer programs and systems.
✓ Policy Creation & Modification: Start with versatile templates. Our intuitive editor ensures policies stay up-to-date.
✓ Users Trained on Policies: Integrate training with policy distribution, turning awareness into actionable defense.
✓ Policy Distribution & Signature: Easy e-signature, tracking, and reminders simplify ensuring company-wide compliance.
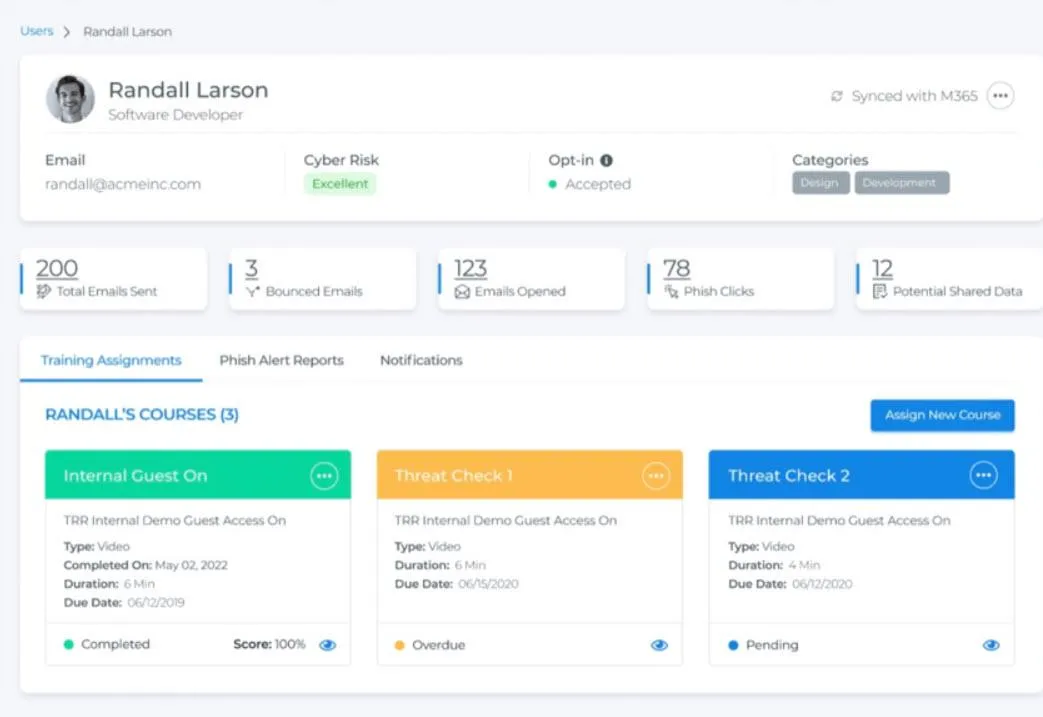
Policy Driven Cyber Awareness Training Transforms Your Workforce
Use Case: Jane, an employee, receives an email that looks like it's from the company’s IT department, asking her to reset her password by clicking a link. Remembering her training, she notices oddities in the email address and the urgent, unprofessional tone of the message—key indicators of a phishing attempt. Instead of clicking the link, she reports the email to the IT department, preventing a potential security breach. This proactive step saved the company from possible data theft and financial loss, illustrating the direct impact of policy-driven cyber awareness education.
How Compliance Sculpted Excellence for A Veteran Manufacturing Company -
A Success Story Profile
In the heart of America’s industrial fabric, there thrives a manufacturing company with a legacy spanning over two decades, steeped in the tradition of excellence and a stalwart partner to the government. The cornerstone of its unwavering success and longevity? A deeply ingrained culture of compliance that has not only safeguarded its contracts but has also elevated it as a model of excellence in the business world today.
The Symphony of Compliance
✓ Education as Empowerment: Every employee, a note in this orchestral masterpiece, plays in harmony, understanding their part in the grander scheme. It's a rhythm of responsibility; a dance of diligence.
✓ Technology as the Conductor: Advanced tools track, train, and amplify compliance, ensuring the entire ensemble plays in unison. It's not just software; it's the maestro leading the charge.
✓ Risks and Emotion in Score: Beyond the numbers, a score of emotional intelligence and risk assessment charts the path forward. This is where data meets discernment—a minimal risk ecosystem ensuring the symphony goes on.
The Crescendo of Benefits
A Fortress of Trust: This approach turns potential pitfalls into pillars of strength.
Government contracts aren't just retained; they're celebrated as milestones of a commitment to compliance.
A Chain as Strong as Its Weakest Link: The ethos of compliance extends beyond the company, enveloping suppliers in a mutual pact of integrity and security. This isn't a supply chain; it's a lifeline of collective resilience.
An Ode to Sustainability: In this narrative, compliance is the muse inspiring growth, innovation, and a legacy of trust. The company doesn't just thrive; it leads, setting the stage for a new era in manufacturing.
The Legacy Continues
In a world obsessed with shortcuts, this manufacturing giant chose the path less traveled—a path where compliance is the cornerstone of excellence. This isn't just a company; it's a testament to the power of integrating compliance into the fabric of business.
This story isn't about the status quo but about envisioning a future where compliance drives creativity, innovation, and enduring success. Here, compliance isn't a hurdle; it’s the key that unlocks true potential, ensuring the legacy of excellence continues.
Boost Your Online Safety with Our 'Protect Your Brand' (Add-On)

Keep your business safe online with our two-part safety net. We watch over your business name and your emails to keep tricksters and hackers at bay by secure your domain and email against impersonation, phishing, and spoofing.
Think of us as your digital lookout, constantly checking for signs of trouble. If we spot something fishy, we'll quickly let you know so you can keep your business secure.
Plus, you can easily track how safe your business is with our simple reports and updates!
This base monthly plan begins at $99/mo includes one user and scales from there. Additional users can be added as needed.
Safeguard Your Online Identity
Proactive Monitoring: Vigilantly scans for domains mimicking yours to prevent impersonation.
Immediate Alerts: Notifies you of potential threats to take swift action.
Preserve Trust: Ensures customers engage with your genuine site, maintaining brand credibility.
Defend Your Communications
Early Detection: Alerts you to suspicious email activities targeting your organization.
Prevent Breaches: Stops phishing and spoofing attacks before they harm your business.
Secure Interactions: Protects internal and customer communications, reinforcing confidence.
Strengthen Your Brand Integrity
Unified Defense: Combines domain and email protection for a layered security approach.
Enhance Trust: Builds stronger customer relationships through demonstrated security vigilance.
Strategic Focus: Frees up your resources to concentrate on growth, not just threat mitigation.
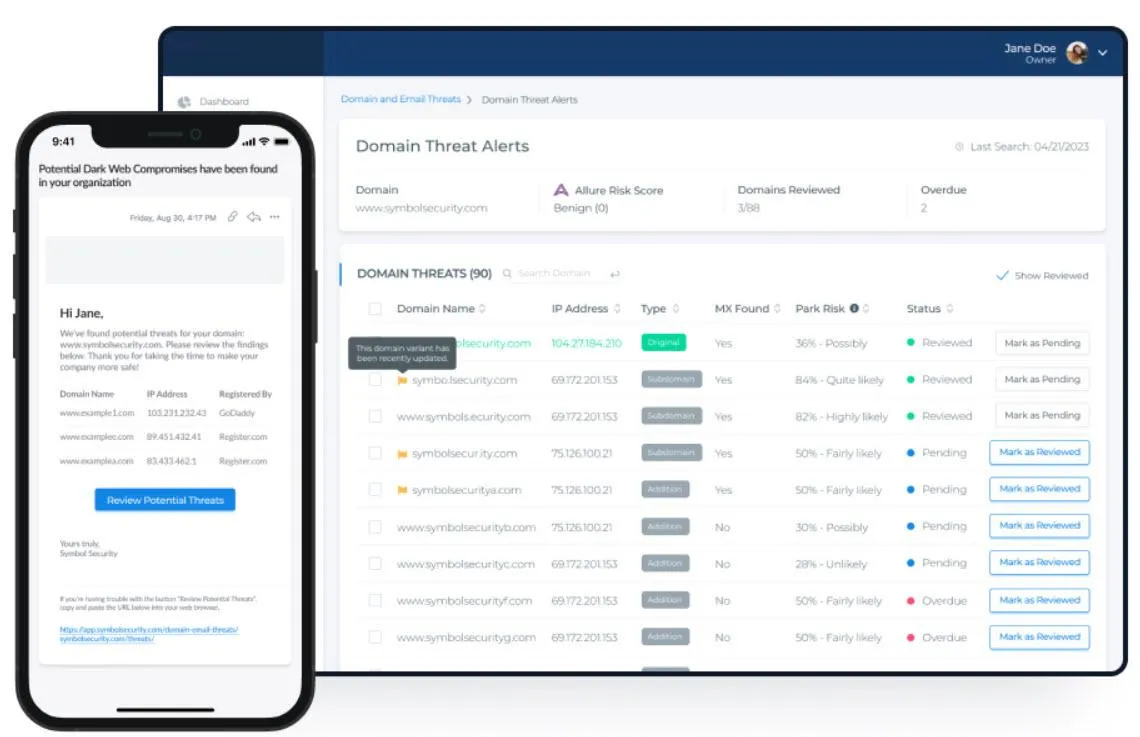
Secure Your Brand's Presence
Combine Domain Doppelganger Protection with Email Threat Alerts for comprehensive brand security.
✓ Proactive Monitoring: Continuously scans for potential impersonation, preserving your brand's integrity.
✓ Real-time Response: Instantly alerts you to threats, enabling swift action to protect your business reputation and customer trust.
✓ Seamless Integration: Effortlessly blends with your existing security setup, enhancing protection without complicating your operations.
What Is A Doppelganger?
A doppelganger is like having an evil twin out there who looks just like you, but isn't related to you at all. It's someone who could be your look-alike or double, appearing so similar that people might have a hard time telling you apart. The term is also used in technology and security to describe websites or domains that try to imitate or pretend to be another, reputable site, to trick people for malicious reasons.

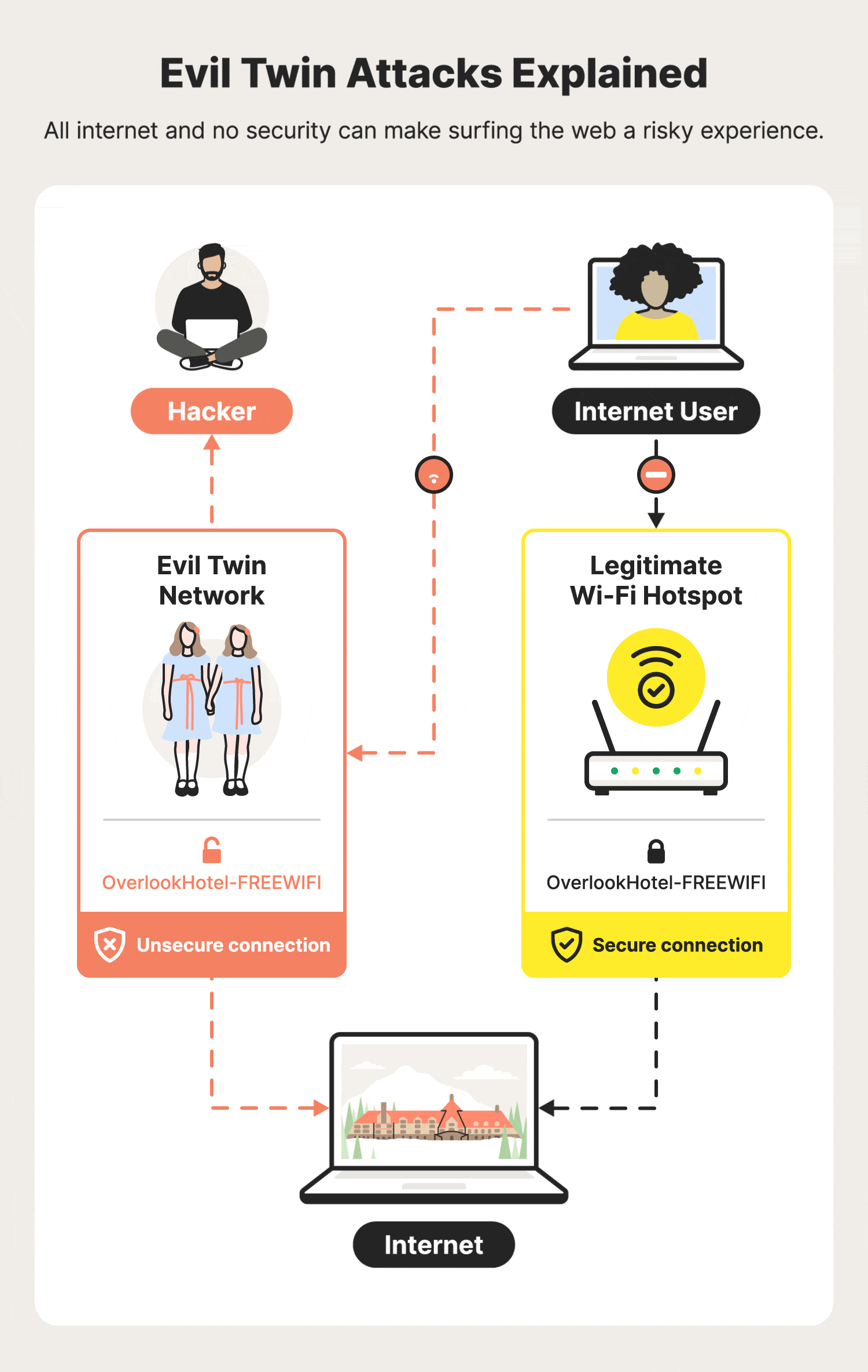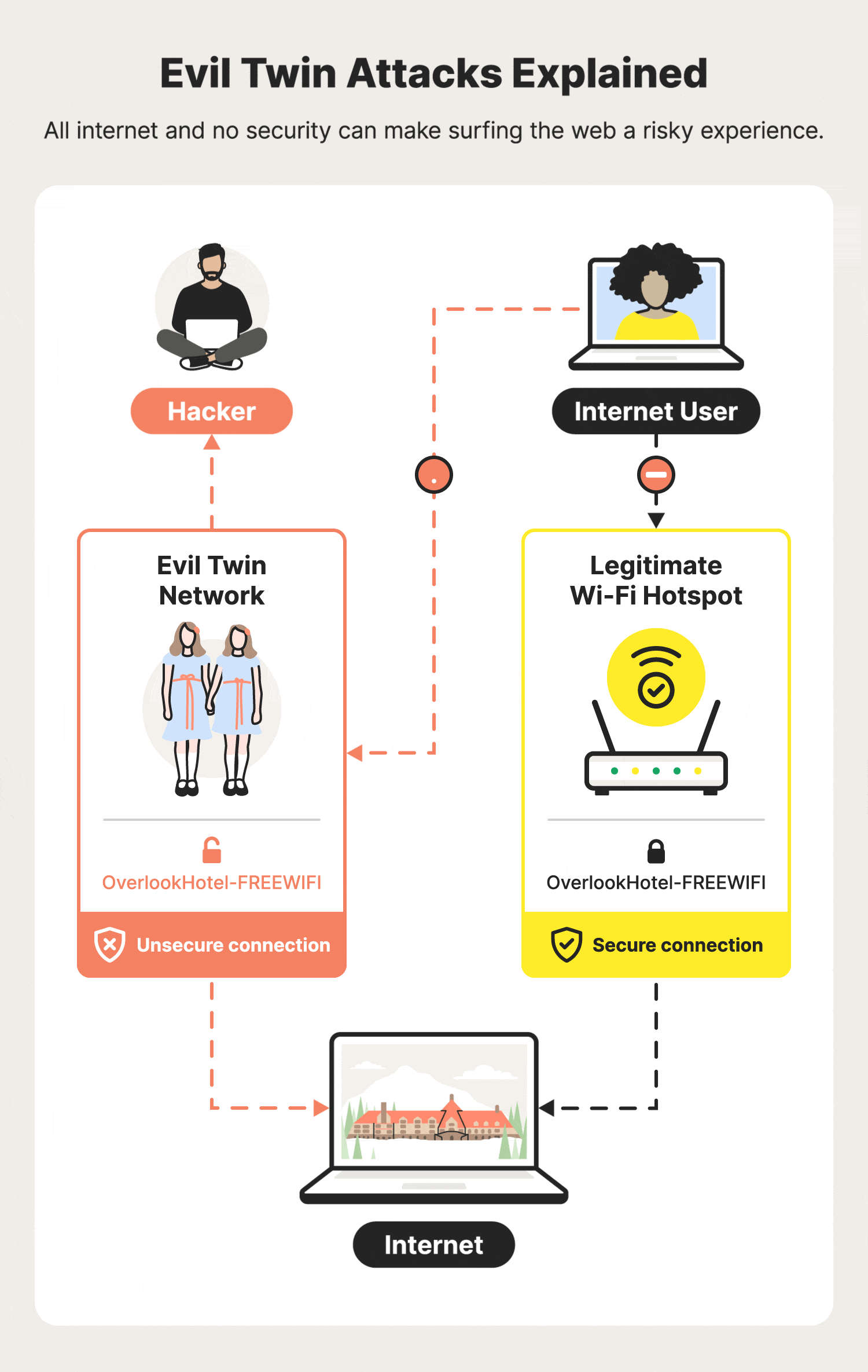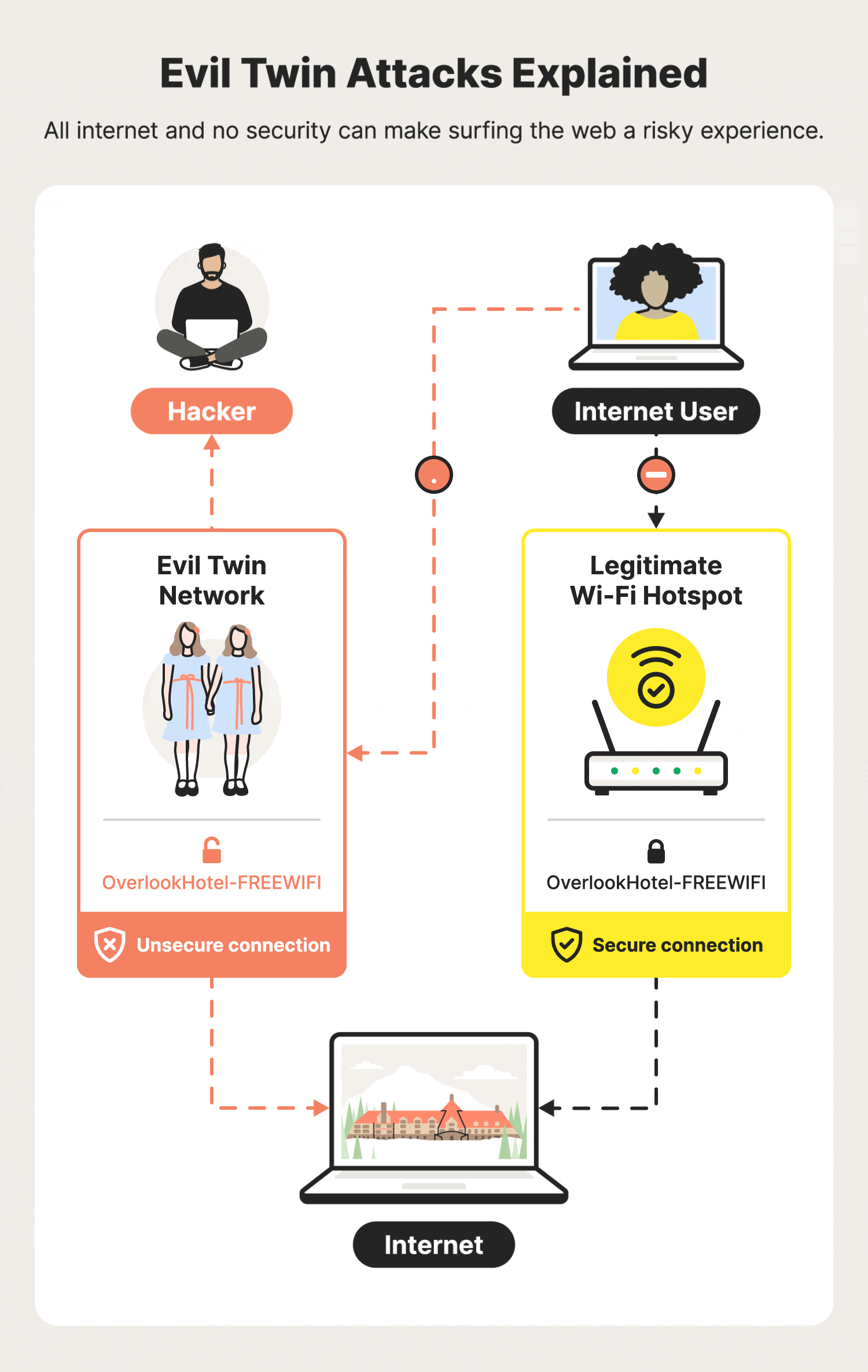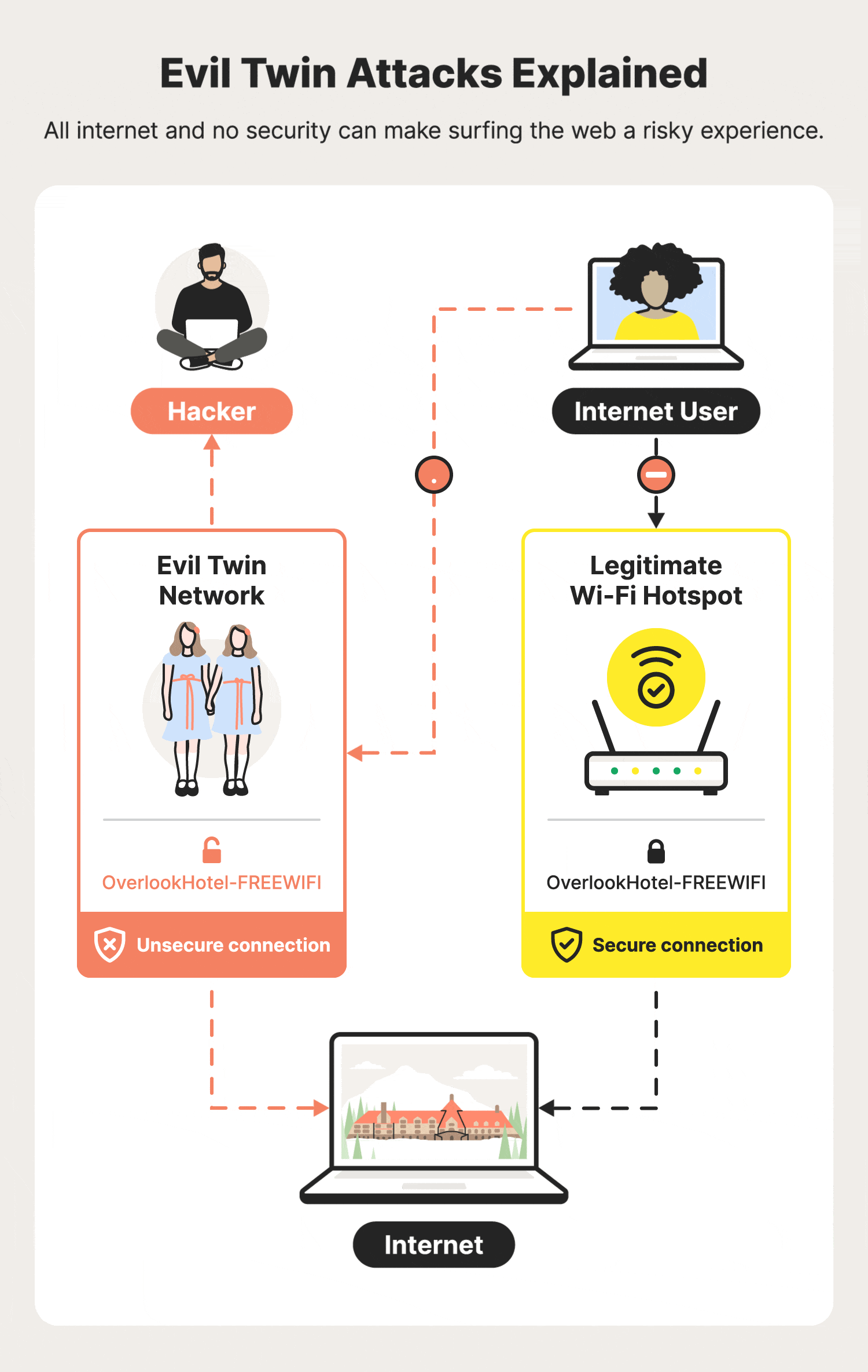
What Is An Evil Twin Attack?
An evil twin attack (also known as a doppelganger) is a sophisticated cyber threat where an adversary fabricates a Wi-Fi network that mimics a legitimate one.
This counterfeit network, designed to deceive, ensnares users into
connecting, believing they are accessing a safe and known Wi-Fi.
Upon connection, the malefactor gains the ability to monitor internet activities, pilfer sensitive data such as login credentials, financial information, and potentially deploy malware.
Identifying and Thwarting Evil Twin Attacks
Double-check Wi-Fi names: Before you connect to any Wi-Fi in public places like coffee shops or hotels, ask the staff for the correct name and password. This helps make sure you're not connecting to a fake network set up by a hacker.
Use a VPN: Think of a VPN (Virtual Private Network) as a secure tunnel for your internet use. It keeps what you do online private, even when you're on public Wi-Fi, making it hard for hackers to see your activity.
Look for the lock: When you're visiting websites, check your browser for a small padlock symbol next to the website's name. This means the site is more secure, and it's harder for hackers to see what you're typing.
Turn off auto-connect: Some devices automatically look for and connect to Wi-Fi networks. This can be risky. It's safer to choose manually which networks you connect to.
Keep your gadgets up to date: Regularly updating your devices and apps means you have the latest security features, which helps keep hackers out.
Learn about online safety: Knowing about the types of tricks hackers use, like fake Wi-Fi networks, means you'll be better at avoiding them.
Notice anything odd?: If something feels wrong, like a website looks strange or you're asked to download something unexpected, disconnect from the Wi-Fi. It might not be safe.
If you're curious about more ways to protect yourself online or have other questions, just ask!
Mastering Domain Defense: Integrating Vigilance Against Email Threats - A Success Story Profile
In the sprawling digital landscape, securing the gateway to your domain is paramount—but the threats do not end there. Email, an essential tool of communication, has become a favored battleground for cyber adversaries. The art of mastering domain defense extends into the realm of email vigilance, where every message could be the trojan horse that breaches your fortress.
The Evolving Battlefield
Understanding that domain doppelgängers and phishing schemes are two sides of the same coin is crucial. These insidious threats cunningly mimic trust, attempting to deceive not just machines, but more critically, your people. It's here, in the inbox's everyday interactions, that your defense strategy must prove indomitable.
The domain doppelgänger doesn't act alone; it's a part of an army that includes compromised and created domains, all weaponized with a singular goal—malware phishing. Over 50% of embedded URLs in phishing campaigns are masks worn by these compromised domains, masquerading as trustworthy beacons. The battlefront is vast, spanning the simplicity of created domains to the legitimate façades of abused services.
Unraveling Deceit
With tact and tenacity, you embarked on a mission to fortify your domain. Using domain monitoring, a vigilant scan of the digital horizon for evil twins lurking in the shadows. Their arsenal? AI-driven phishing simulations and real-time threat alerts. Each fake profile on social media, every dubious app in the store, found itself under relentless scrutiny.
Harnessing AI for Email Vigilance
The integration of AI-driven simulations into your cybersecurity arsenal transforms passive defenses into active deterrents. Effortlessly reducing phishing threats by 97%, these automated simulations are your knights in digital armor. They do not merely guard; they train your workforce to be the first line of defense, vigilant sentinels who can identify and neutralize threats with a glance.
Immediate Insights, Immediate Action
The beauty of an AI-driven platform is its ability to tailor content to individual skills, ensuring each user receives relevant, impactful training.
Administrators are empowered with immediate insights, turning the vast expanse of your organization into a tightly knit community of cyber defenders.
Launch hyper-realistic phishing simulations in seconds, a testament to how nimbleness and precision can elevate your cybersecurity efforts exponentially.
Transforming Mistakes into Victory - The Shield of Education
But the true power lay in your team. Through training sessions and checkpoints, you ingrain cyber hygiene practices into the very fabric of your culture. Employees, now versed in the art of spotting real-life threats, became the company's strongest defense. One click could now disarm potential breaches, turning every team member into an active participant in safeguarding the domain.
In this narrative of vigilant domain and email defense, mistakes become invaluable lessons rather than vulnerabilities. A user's misstep, clicking on a phishing simulation, unfolds into a moment of nanolearning.
These instant lessons explain what veered off path and how to sharpen one's vigilance for future encounters, effectively turning potential breaches into opportunities for strengthening your cyber defenses.
A Comprehensive Strategy for Cyber Resilience
Through training sessions imbued with cyber hygiene practices and punctuated by timely threat alerts, a culture of cybersecurity mindfulness is cultivated. This comprehensive strategy not only shifts user behavior but molds it into a formidable shield against the multifaceted threats assailing your organization.
A Legacy of Vigilance - Embarking on a Journey of Cybersecurity Excellence
As you navigate through the treacherous waters of cyber threats, integrating vigilant practices against domain doppelgängers and email phishing becomes your narrative of resilience. This story is not just about defending your domain; it's about safeguarding your legacy, ensuring that every layer of your digital realm stands tall against the ever-evolving threats. In embracing these advanced tools and practices, you're not merely surviving; you're thriving in the digital age, a beacon of trust and security in an ever-evolving digital landscape. The journey to mastering domain defense is yours—a saga of vigilance, innovation, and indomitable spirit.
The power of proactive defense in the realm of cyber defense, the domain serves as the front line, and you stands tall, a bastion of trust and security in an ever-evolving digital landscape. Your journey underscores a profound truth: in the fight against cyber threats, knowledge, and vigilance are the most formidable weapons.

Proactive Dark Web Monitoring (Add-On)
Uncover and mitigate invisible threats with our Dark Web Cyber Threat Surveillance by monitoring the Darknet and chat rooms to identify harmful sentiment and potential attacks against your Systems, Brand, and Key Employees.
Our solution helps you protect your brands from being damaged through incorrect or malicious association on the Deep Web, Dark Web, and Social Networks.
Uncover Invisible Threats
Cybercriminals build specific attacks targeted at people or companies. Stay one step ahead of these crimes with early detection by identifying potential risks lurking within the dark web, ensuring that your systems and brand are safeguarded against covert operations aimed at undermining your integrity.
Affordable, Unmatched Protection
Leverage advanced surveillance technology at a cost designed to fit the budgetary considerations of small and medium-sized businesses, making top-tier cyber defense accessible without compromising on quality by offering unmatched visibility into the potential for cybercrime and reputation damage
Guard Your Digital Privacy
Maintain the security and trustworthiness of your online presence. Continuous monitoring offers peace of mind against
VIP executive targeting, post breach activities, slander campaigns, brand damage or other misinformation preserving your organization’s integrity and customer trust.
Proactive Dark Web Monitoring
Stay ahead of invisible threats with early detection across the dark web with Cyber Threat Surveillance.
✓ Uncover Invisible Threats: Monitor for risks that could undermine your organization's integrity and security.
✓ Affordable Protection: Our surveillance technology fits SMB budgets, providing premium cyber defense.
✓ Plans begin at $1400/yr: This base annual plan includes one domain and two key words. Additional domains and keywords are available for purchase at additional costs. Three year commitment.
What Is the Dark Web?
The dark web is a hidden part of the internet that you can't find or access through regular browsers or search engines like Google. It requires special software to get into, making it anonymous and private. Think of the internet as an iceberg: what we normally use is just the tip above water, but the dark web lies beneath the surface. It's known for keeping users' identities secret and is often associated with privacy protection, but it can also be used for illegal activities due to its anonymity.
The Enlightened Path to Dark Web Mastery - A Success Story Profile
Imagine embarking on a mission into the shadowy realms of the internet —a place not charted by conventional maps, where the digital air thickens with plots and secrets. This, my friends, is not the start of a dubious 90s thriller but the reality of the dark web's hidden corridors. Yes, indeed, the dark web might as well star in its own film, "The Dangers You Can't Google" because this part of the internet is as elusive as a good movie plot in a world overrun by remakes.
The Dark Web Decoded
Picture this: 31% of U.S. adults scratch their heads at the mention of the dark web. A survey whispers that a mere 21% could claim "very familiar" status, with another 48% hovering at "somewhat familiar." The rest? They're as clueless as someone trying to solve a Rubik's Cube in the dark.
This hidden internet slice, accessible only by the digital spelunkers using specialized software like Tor, has become the Wild West of online markets—all hats, no cattle—where you can find everything from stolen passwords to the recipe for your grandma’s lost cookies. But mainly stolen passwords.
Why is Everyone Whispering About the Dark Web?
It's not just a playground for the cyber-sinister; it's also a treasure trove for the digital vigilante, the proactive protector of their domain. This seedy underbelly is bustling with illicit trades, including your precious data. Enter the cyber knight in shining armor: dark web monitoring.
Harnessing the Shadows
Now, let's say you decide to go superhero mode, cloak twirling as you dive headfirst into this abyss to safeguard your digital treasures. You'd need some gadgets, right? Think Batman, but for the internet. Dark web monitoring stands as your Batmobile, revved up with AI-driven tools that sniff out data leaks with the efficiency of a bloodhound.
Action! Cue Heroic Montage
Imagine deploying a fleet of digital scouts across the dark web. They're on a hunt—real-time alerts at the ready, predictive threat analysis lighting the way. They're not just looking; they're finding. Compromised credentials, whispered deals, all laid bare before their unblinking eyes. Your mission? To customize this cloak-and-dagger operation, scaling it, integrating it, transforming your employees into a league of cyber guardians through continuous training and improvement.
Turning the Lights On
It turns out, dark web monitoring is your Gandalf in the Mines of Moria—bringing light to dark places, revealing traps and treasures alike. This isn't just about batting away cyber goblins; it's about arming yourself with knowledge, detecting leaks and threats, and responding with the speed of a gazelle—or at least an internet connection not powered by hamsters.
A Vision for the Future
As you stand vigilant against the dark arts of the web, you're not just defending your domain; you're telling a tale of resilience and preparedness. With dark web monitoring, every business, no matter its size, can turn the tables on cyber threats.
You're not waiting for the storm; you're tracking the clouds, ready to dance in the rain—or dispatch it, with a click of your techno-magical umbrella. In this enlightened quest for domain defense, dark web monitoring shines as a beacon of proactive protection.
Your legacy? A saga of security, a story of overcoming the shadows. And remember, friends, in the grand narrative of cyber defense, it's better to light a candle than curse the darkness—or at least, deploy a really sophisticated dark web monitoring tool.
Enhance your protection with our Comprehensive Bundle, including DataSafe Compliance, Domain and Email Threat Alerts, Deep Web Cyber Threat Surveillance, and access to a phishing simulation and training platform, all accompanied by expert guidance. Opt for our annual plan and enjoy a 20% saving. Reach out for personalized, per company/month pricing.
LEARN MORE
MSP • vCISO • PARTNER INFORMATION
Fortifying Digital Frontiers: Your Bridge Over Cyber Breaches
© 2026 Cyber Secure Online LLC | All Rights Reserved