Protect Your Business from Cyber Threats—
Even Without a Tech Team
Enterprise-grade security at a price even small businesses can afford.
Worried that remote work leaves you exposed? Protect your company from hackers,
insider threats, and costly mistakes—no IT expertise required.
Simple Steps to Get Started: Don’t let a single mistake cost you everything.
No tech jargon: We explain what you need, why you need it, and how it keeps your business running safely.
You’re not alone: Most small business owners think antivirus or firewalls are enough—but today’s threats go much further.
Real stories, real protection: Learn how Jake Baker lost his business overnight—and how you can avoid the same fate.

Protect Your Business from Cyber Threats—
Even Without a Tech Team
Enterprise-grade security at a price even small businesses can afford
Worried that remote work leaves you exposed? Protect your company from hackers,
insider threats, and costly mistakes— no IT expertise required
Simple Steps to Get Started: Don’t let a single mistake cost you everything.
No tech jargon: We explain what you need, why you need it, and how it keeps your business running safely.
You’re not alone: Most small business owners think antivirus or firewalls are enough—but today’s threats go much further.
Real stories, real protection: Learn how Jake Baker lost his business overnight—and how you can avoid the same fate.

Jake Baker, a Small Business Owner
Imagine losing $5 million overnight.
Sadly, Dr. Jake Baker did lose that amount due to an insider cyber attack. His story is a stark reminder: proactive cybersecurity is no longer optional; it's essential for survival.
"After an insider cyber attack cost us $5 million, I learned the hard way that proactive cybersecurity isn't optional—it's fundamental." - Dr. Jake Baker
This story isn't merely a warning—it's a call to action.
Every business must prioritize cybersecurity to protect itself from devastating losses and safeguard its future.

Jake Baker's life changed over-night!
What Makes Us Different—and Why It Matters to You
Most small business owners think they’re protected because they have antivirus or a firewall. The truth? That’s just the start.
Cyber attacks and costly mistakes can wipe out a business overnight—especially with remote workers, personal devices, and no IT team to watch over things.
Our approach is built around you. We seamlessly integrate with the tools and workflows your business already uses, so you get protection without disruption.
Here’s how we keep you safe...
Comprehensive
We cover all the ways your business can be attacked, not just the obvious ones.
Operations
No tech team needed. We handle the setup, monitoring, and alerts—so you can focus on running your business.
Remote work?
No problem.
Your team is protected whether they’re in the office, at home, or on the go.
Cost?
Clear, predictable pricing. No surprises, no hidden fees. You’ll always know what you’re paying for.
Support
Real help, when you need it. If something suspicious happens, our experts are there to guide you—no confusing tech talk.
Ready to Experience Always-On Guard? It's Easy ...

Schedule Your Intro Call
We’ll quickly identify your unique cybersecurity needs and show you how Always-On Guard can effectively protect your digital world.

Activate Your 14-Days
Get full support from our expert team, ensuring a seamless and valuable trial with no obligations.

Strategy Session Review
Together, we’ll fine-tune and customize your cybersecurity strategy to perfectly fit your business needs.
Experience real people watching over your business around the clock—so you don’t have to worry about cyber threats, day or night.
Our Security Operations Center (SOC) team monitors your business 24/7, using advanced detection tools to spot threats as soon as they appear.
If something suspicious happens—even in the middle of the night—our experts step in right away to keep your business safe.
We provide easy-to-understand training for your team, so everyone knows how to spot scams and respond to threats.
You get enterprise-grade protection, without the cost or complexity of hiring your own IT staff.
After your free trial, continue seamlessly at $79/user/month—no surprises, no hassle.

Automatic Safety
Our advanced intelligence tools work tirelessly in the background, providing superior protection against zero-day cyber threats while empowering your team to focus on what matters most.
Smarter Work, Not Harder
In just two weeks, experience how our services enhance your operations by automating complex security tasks, leading to more efficient workflows.
Less Hassle for Your Team
By automating routine security processes, we enable your IT personnel to concentrate on strategic initiatives that drive business growth.
Seamless Integration
Our flexible services integrate effortlessly with your existing processes, enhancing security without disrupting your established workflows.
CSO's Proactive Security Awareness Training
68% of breaches involve human error. Strengthen your security posture by
combining real-world simulations with engaging training.
Reduce your risk by transforming employees into a proactive human firewall
with adaptive, interactive learning.
Phishing Simulation
Engaging Compliance Courses
Adaptive Training
Scheduled Training
Reporting Suite
User Feedback
Empower your team—make security second nature.
Speak to a cybersecurity expert and get a free risk assessment for your business.
95% Automation with AI & Human Expertise
We strive to be your trusted partner in safeguarding your digital assets-not just another vendor. By combining the power of AI, machine learning, and our SOC 2-certified Security Operations Center, we automate up to 95% of your cybersecurity operations.
Most small businesses leave costly gaps and lack expert support by patching together basic tools like antivirus, firewalls, or email security.
Cybercriminals exploit these weaknesses - targeting email, remote work, WiFi, cloud apps, and even your employees.
We proactively safeguard your business across 14 critical risk areas, closing those gaps with unified, expert-backed protection-so you can operate with confidence and focus on what matters most.
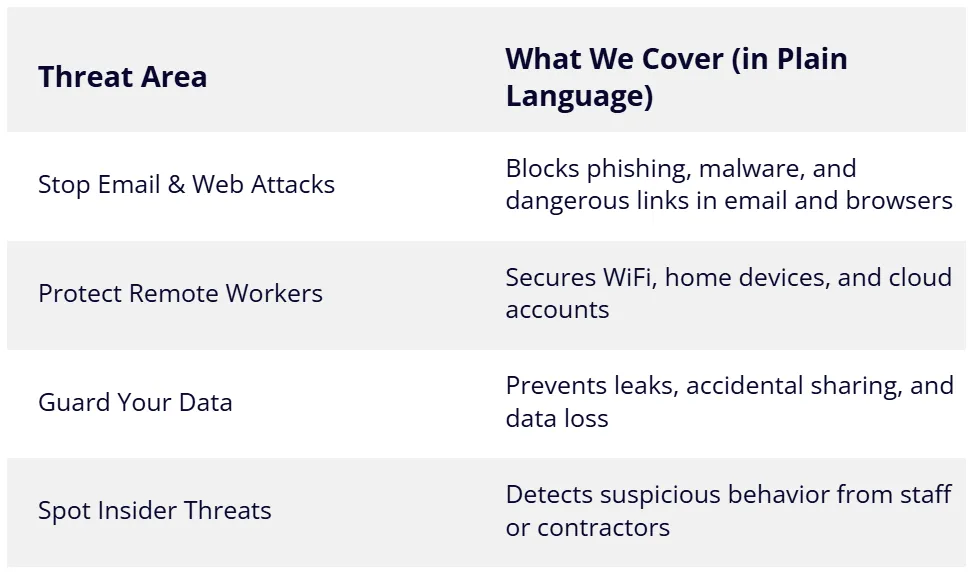
Threat Area
What We Cover (in Plain Language)
Stop Email & Web Attacks
Blocks phishing, malware, and dangerous links in email and browsers
Protect Remote Workers
Secures WiFi, home devices, and cloud accounts
Guard Your Data
Prevents leaks, accidental sharing, and data loss
Spot Insider Threats
Detects suspicious behavior from staff or contractors
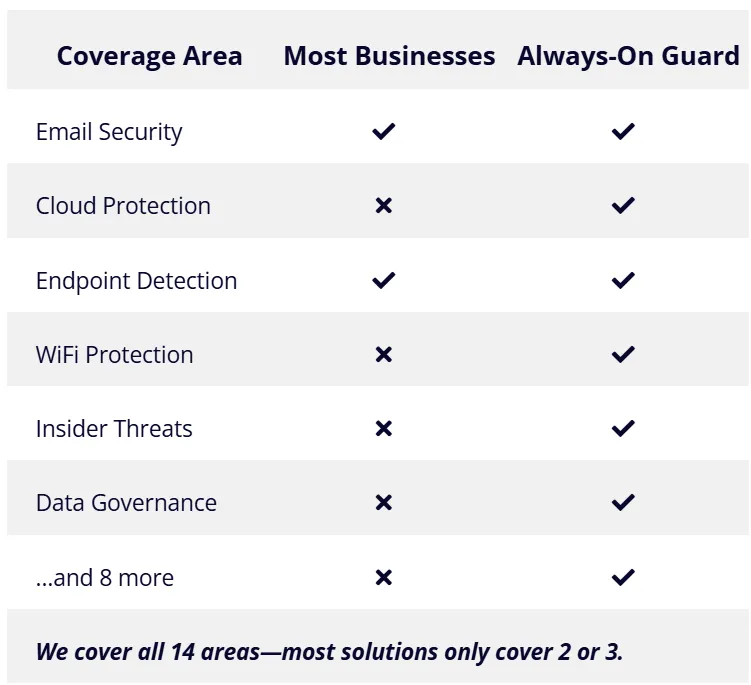
What Most Businesses Have ”vs“ What You Get With Always-On Guard
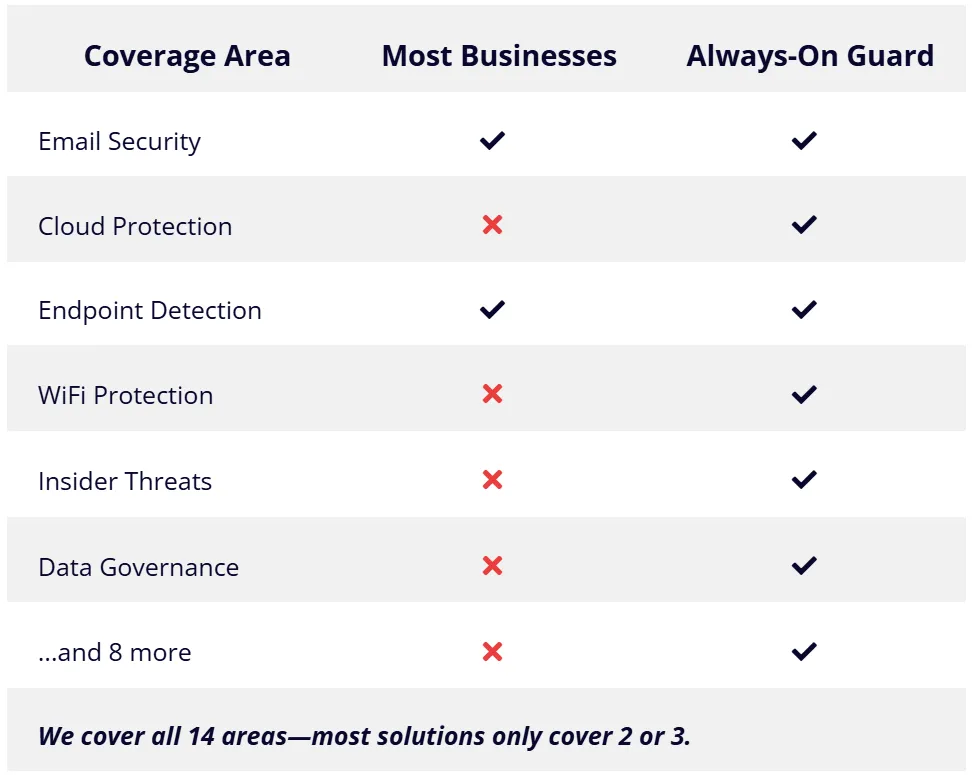
Coverage Area
Most Businesses
Always-On Guard
Email Security
Cloud Protection
Endpoint Detection
WiFi Protection
Insider Threats
Data Governance
...and 8 more
We cover all 14 areas—most solutions only cover 2 or 3.
14 Critical Risk Areas Covered in Always-On Guard

We cover 14 areas—most solutions only cover 2 or 3.
Cyber threats don’t just come through email. We cover every way your business can be attacked—
so you don’t have to wonder what’s missing.

BEFORE Cyber Secure Online
Stop Email & Web Attacks: Block phishing, malware, and dangerous links.
Protect Remote Workers: Secure WiFi, home devices, and cloud accounts.
Guard Your Data: Prevent leaks and accidental sharing.
Spot Insider Threats: Detect suspicious behavior from staff or contractors.

AFTER Cyber Secure Online
Why Choose Always-On Guard? Your Competitive
Advantage in Cybersecurity
In today's digital landscape, cybersecurity isn’t just protection—it helps you keep your customers and win new business and it's a strategic asset that sets businesses apart from your competitors. By choosing Always-On Guard, you're not just protecting your business from threats; you're gaining a competitive edge.
Here's How We Help You Stand Out:
Experience the Always-On Guard Advantage
Strengthen Trust and Loyalty:
Customers trust you more when they know their information is safe. That means more repeat business and better word of mouth.
Drive Digital Transformation Securely:
You can use new tools and work from anywhere—without worrying about hackers or data leaks.
Enhance Reputation and Differentiation:
Show clients you take security seriously. Stand out from competitors who don’t.
Avoid Disqualification and Delays:
When bidding for contracts, you’ll meet security requirements—so you don’t lose out on deals.
No Hidden Fees:
One simple price—no surprises or extra charges.
Elite Managed Detection & Response:
Real people watch over your business 24/7 and step in if something looks suspicious.
Advanced Security Features:
We block fake WiFi scams, keep your team’s data private, and stop dangerous emails before they reach you.
Effortless Compliance & Automation:
We help you follow the rules for your industry and take care of most security tasks for you—so you can focus on your business.
Why Choose Us Over the Rest?
Always-On Guard Offers Comprehensive Protection at Unbeatable Value
Discover the unparalleled cybersecurity features and unmatched affordability of our solution, designed for businesses seeking robust protection without complexity or hidden costs.
FEATURES
CSO's Always-On Guard
CrowdStrike
SentinelOne
Bitdefender
Endpoint Security (Next-gen AV)
✅
✅
✅
✅
Email Security (Malware, Phishing)
✅
$$
$$
$$
Cloud Security (O365, GSuite, etc.)
✅
$$
$$
$$
EDR (Endpoint Detection & Response)
✅
✅
✅
$$
Network Security (VPN, Firewall)
✅
$$
$$
$$ Partial
Data Governance (Endpoint, User Data)
✅
$$
$$
❌
WiFi Phishing Protection
✅
❌
❌
❌
For the best viewing experience, please rotate your device to landscape mode.
Inbound Email Gateway
✅
❌
❌
❌
Secure Web Gateway
✅
$$
$$
$$
User Data Governance
✅
❌
❌
❌
Pricing (per user/month)
$129
$160+
$160+
$110
Ready to secure your business with our all-in-one solution?
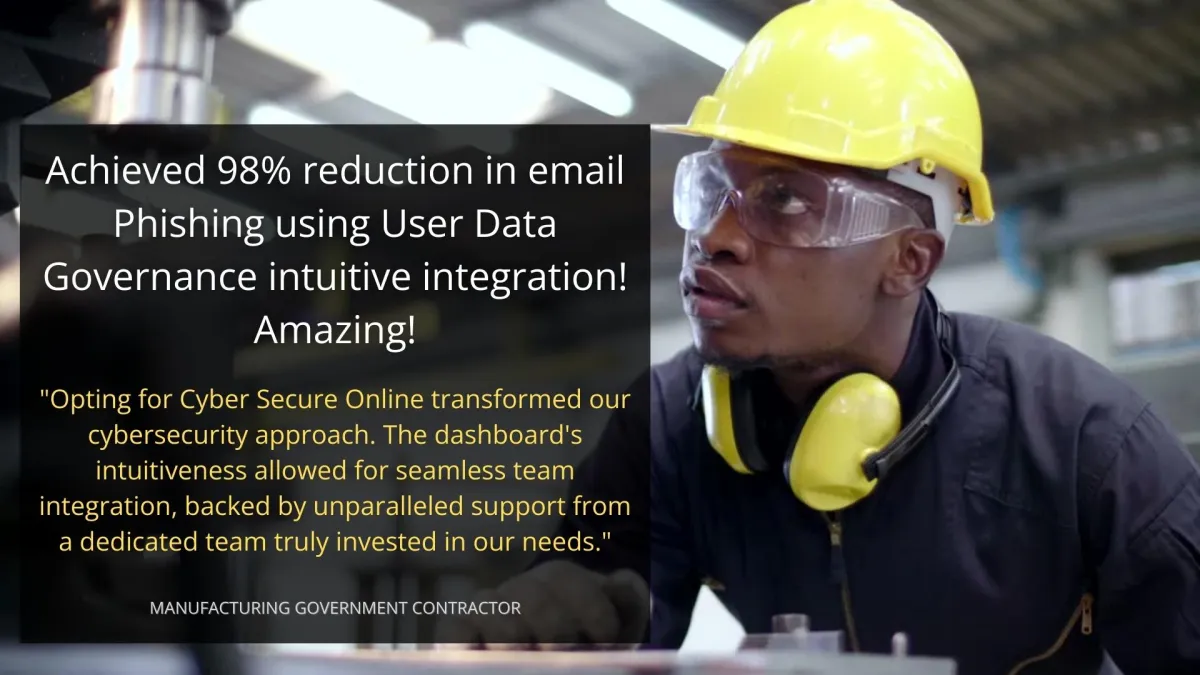
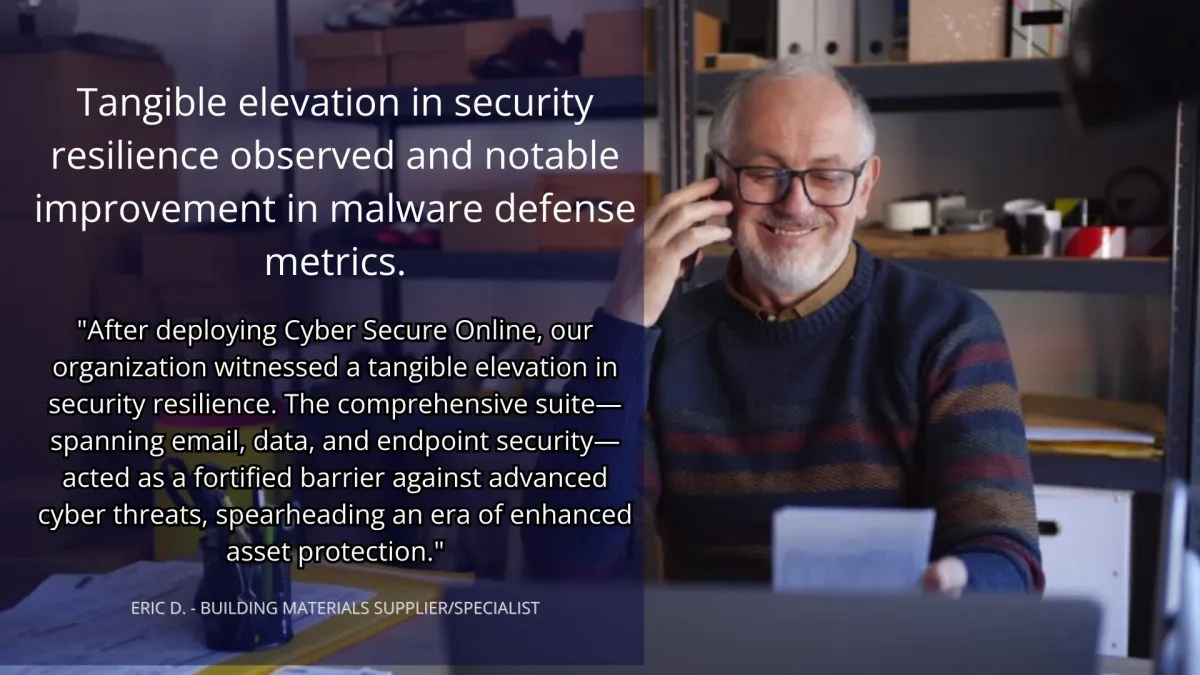
SEE WHAT OUR CLIENTS ARE SAYING...
Meet Our Team
We’re a dedicated team who cares about your business—just like you do.
When you reach out to Cyber Secure Online, you’re connecting with real people who understand the challenges of running a small business in today’s digital world.
We’ve spent years helping business owners stay safe from cyber threats, and we’re here to guide you every step of the way—no tech jargon, no runaround.
If you ever have a question or need help, you’ll talk to one of us, not a robot. We’re here to make cybersecurity simple, so you can focus on what matters most: your business.





Cybersecurity 'Digital Health Check' FAQs
Empower your organization with essential knowledge to navigate the complexities of
cybersecurity and ensure robust protection against digital threats.
What is Always-On Guard (AOG)?
Always-On Guard (AOG) covers 14 critical areas of cyber risk—most solutions only cover 2 or 3. Our service that protects your business from hackers, scams, and costly mistakes. You get protection in all the ways small businesses are targeted—so you can stop worrying about cyber threats.
How does AOG protect my business?
AOG keeps your business safe by:
¤ Blocking scam emails and dangerous links.
¤ Protecting files and data in your cloud accounts (like Google, Microsoft, Dropbox).
¤ Watching for suspicious activity on your computers and devices.
¤ Keeping your team safe when they work from home or use public WiFi.
¤ Making sure only the right people can see sensitive information.
With these protections, you’re covered in all the ways small businesses can be attacked.
What makes your pricing model unique?
You pay one simple price— $79 per user each month. There are no extra charges or hidden fees. Everything you need is included.
How can I try AOG before committing?
Try Always-On Guard free for 14 days. No credit card needed, no obligation—just see how it works for your business.
What happens after the trial period?
After your free trial, you can keep your business protected—no interruptions, no hassle.
You’ll get ongoing 24/7 monitoring, expert support, and coverage in all the ways small businesses are targeted.
If you love the peace of mind you’ve gained, simply continue for a predictable monthly subscription (per user).We’ll check in during your trial to answer questions and make sure you’re getting the most out of the service.
How does AOG integrate with my existing IT systems?
AOG is easy to set up and works with the tools you already use, like email and cloud storage. Our team helps you get started, and you won’t need to change how you work.
What kind of support do you provide?
We’re here to help you every step of the way:
¤ We set everything up for you.
¤ Our team watches for threats 24/7 and steps in if there’s a problem.
¤ You get regular check-ins and easy-to-understand training for your team.
¤ If you ever have a question, just fill out a support ticket or email us.
Why is cybersecurity important for small businesses?
Cyber attacks can put small businesses out of business—sometimes overnight. Most attacks target companies just like yours, and the costs can be huge. For example:
1. 64% of all cyberattacks target small businesses.
2. The average cost of a data breach for small businesses can reach approximately $200,000.
3. Most customers won’t come back after a data breach.
In today’s digital age, proactive cybersecurity is essential for success.
Can you explain the DataSafe Industry Compliance Training?
DataSafe Training helps your team spot scams, follow the rules for your industry, and keep your business safe. It’s easy to use, keeps you up to date with regulations, and helps your staff know what to do if something suspicious happens.
How do I get started?
Getting started is easy:
1. Watch the quick demo or talk with our team about your needs.
2. Start your free 14-day trial—no credit card needed.
3. We’ll help you get set up and check in to make sure everything’s working.
4. Decide if you want to keep your protection going.
We’re here to help you every step of the way.
Book a Free Consult Call
Ask about your business needs
Book a LIVE DEMO
Ask about your business needs
Subscribe to Learn More
I agree to receive communications from the Cyber Secure Online.
MSP • vCISO • Service Providers & Partner Information
Fortifying Digital Frontiers: Your Bridge Over Cyber Breaches
© 2025 Cyber Secure Online LLC | All Rights Reserved