1-888-988-5567
Cyber Secure Online - "The HUB"
Addressing The Crisis At Hand
The HUB
The Day My Company Died (And What I Learned From It)
A simple “trojan horse” malware and wired $1.1 million out of their accounts. No one came to the rescue. ...more
Data Breach ,Cost of Cyber Crime Compliance Remote Workforce Security Risk Third Party Risk &Mobile Security
August 31, 2025•1 min read

I Hired a Hacker to Infiltrate My Company
The most dangerous attackers often aren't breaking in-they're already inside, watching, adapting, and waiting for the perfect moment to strike. ...more
Data Breach ,Cost of Cyber Crime Compliance Remote Workforce Security Risk Third Party Risk &Mobile Security
August 29, 2025•1 min read
How to Protect Your Business from Phishing Scams
How can I be sure my business is protected from scams and phishing emails without hiring a full IT team? ...more
Data Breach ,Data Protection Cost of Cyber Crime Cyber Crime Best Practices Compliance Remote Workforce Access Governance Risk Risk Management Third Party Risk Internet of Things (IoT) Mobile Security healthcare &Ransomware
August 24, 2025•1 min read

The Truth About Hacking (and Hackers)
Sharing one of our clients personal journey of discovery and the surprising revelations he uncovered about the world of hacking. ...more
Data Breach ,Cyber Crime Best Practices Compliance Technology Privacy Remote Workforce Risk Management Third Party Risk DDos Internet of Things (IoT) Mobile Security healthcare &Zero-Day
August 21, 2025•2 min read

How Customer-Centric Cybersecurity is Changing the Game
Cybersecurity has evolved far beyond its roots as a purely technical or IT concern. Today, it is a core pillar of customer trust, brand reputation, and business success. ...more
Data Breach ,Data Protection Cyber Crime Compliance Technology Password Privacy Remote Workforce Security Risk Risk Management Third Party Risk DDos healthcare &Zero-Day
August 18, 2025•2 min read

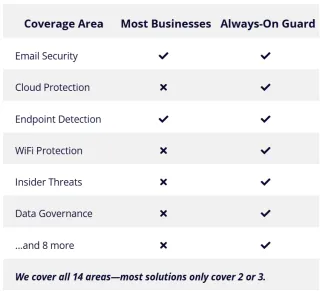
Always-On Guard vs CrowdStrike
Always-On Guard vs CrowdStrike Comparison ...more
Data Breach ,Data Protection Cyber Crime Compliance Remote Workforce Security Risk Access Governance Risk Management Mobile Security healthcare &Zero-Day
April 28, 2025•1 min read
Securing Our Digital Frontiers: United Against Cyber Threats
In an era where cyber threats loom larger than ever, Cyber Secure Online stands as a beacon of hope and resilience. From cybercriminals to hostile nation-states, our enemies are relentless in their ... ...more
Data Breach ,Data Protection Cost of Cyber Crime Cyber Crime Best Practices Compliance Technology Remote Workforce Security Risk Access Governance Risk Risk Management Internet of Things (IoT) healthcare Zero-Day &Ransomware
June 04, 2024•1 min read

Unlock Your Hidden Talents: Transform Your Skills into Success with Simplify System
Dive into the world of entrepreneurship with Simplify System and turn your unique talents into a thriving business. In today's volatile job market, waiting for opportunities to find you isn't just r... ...more
Data Breach ,Data Protection Cost of Cyber Crime Cyber Crime Best Practices Compliance Technology Remote Workforce Security Risk Access Governance Risk Risk Management Mobile Apps Zero-Day &Ransomware
May 15, 2024•1 min read

Simplify System: Your Security, Streamlined
What is Simplify System? Simplify System is an all-in-one platform from Cyber Secure Online that integrates secure communication and resource management, offering advanced security features tailored f... ...more
Data Breach ,Data Protection Cost of Cyber Crime Cyber Crime Best Practices Compliance Technology Remote Workforce Security Risk Access Governance Risk Risk Management Mobile Apps Mobile Security healthcare Zero-Day &Ransomware
May 08, 2024•1 min read

Unlocking True Cybersecurity: The Urgent Need for Third-Party Assessments
In today's cyber landscape, the illusion of security is shattered by frequent breaches and hacks, exposing a critical gap in expertise. This video reveals the hidden vulnerabilities within organizat... ...more
Data Breach ,Data Protection Cost of Cyber Crime Cyber Crime Best Practices Compliance Technology Remote Workforce Security Risk Access Governance Risk Risk Management Internet of Things (IoT) healthcare Zero-Day &Ransomware
May 01, 2024•1 min read

Zero Day Alert: Intercept Cyber Threats Before They Strike
In today’s rapidly evolving digital environment, the threats lurking in the shadows of your digital realm pose a constant risk to the integrity of your systems. With our Third-Party Assessment servi... ...more
Data Breach ,Data Protection Cost of Cyber Crime Cyber Crime Best Practices Compliance Technology Privacy Remote Workforce Security Risk Access Governance Risk Risk Management Internet of Things (IoT) healthcare Zero-Day &Ransomware
April 24, 2024•1 min read

Broken Trust: The Country Club Cyber Breach Unveiled | True Story
In an unforeseen breach, a serene day turns chaotic for country club members as alerts signal unauthorized activities in their bank accounts. This documentary-style video unfolds the chilling narrat... ...more
Data Breach ,Data Protection Cost of Cyber Crime Cyber Crime Best Practices Compliance Technology Remote Workforce Security Risk Access Governance Risk Risk Management Internet of Things (IoT) healthcare Zero-Day &Ransomware
April 17, 2024•1 min read

Book Your Free Consult & Assessment
Start your security journey with a real conversation—no forms, no sales scripts.
When you reach out, a cybersecurity expert will work with you to truly understand your business or personal security needs.
We listen first and answer your questions, making sure Always-On Guard is a fit for you (not the other way around).
No credit card required. No pressure. Just practical guidance.
Step 1: Free Consultation
Call (972) 777-5572 or click the button below...
Enjoy a real, live conversation with our team—
tailored to your specific situation.
Step 2: Personalized Assessment
If you’re a match, we’ll walk you through a quick, 10-question assessment to pinpoint your cybersecurity needs. This isn’t a generic web form—it’s a guided, expert process.
Step 3: Free 14-Day Trial Onboarding
Once you complete your assessment, our team will schedule and guide your risk-free 14-day onboarding trial—so you can experience full protection, with zero commitment.
Call +1 866-943-5763 or click the button below...
LEARN MORE
MSP • vCISO • PARTNER INFORMATION
Fortifying Digital Frontiers: Your Bridge Over Cyber Breaches
© 2026 Cyber Secure Online LLC | All Rights Reserved