1-888-988-5567
Cyber Secure Online - "The HUB"
Addressing The Crisis At Hand
The HUB
I Hired a Hacker to Infiltrate My Company
The most dangerous attackers often aren't breaking in-they're already inside, watching, adapting, and waiting for the perfect moment to strike.
Introduction
The Real Risks
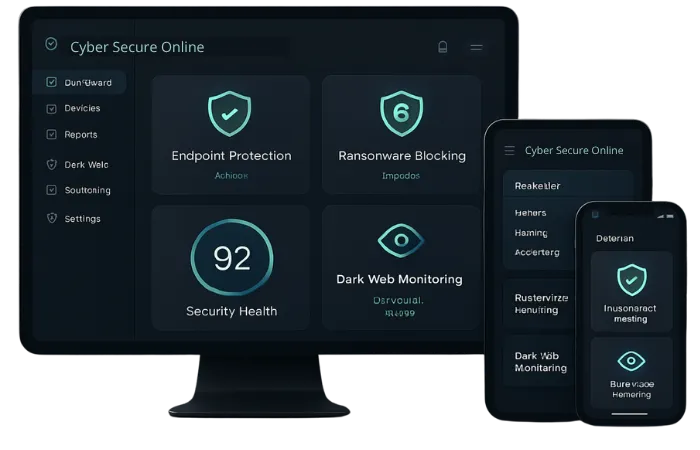
Platform Defense Approach
Cyber Secure Online’s platform leverages a structured triage process:
Scoring and prioritizing risks using behavioral baselines and anomaly detection.
Early identification of potential threats through user behavior analysis.
The system aims to be proactive, stopping hackers before significant damage occurs.
Common Hacking Methods
Zero-Day Exploits: Attacks using vulnerabilities unknown or unpatched by software companies.
Real-World Examples
Phishing Attack: An employee at a major tech company received a legitimate-looking phishing email, entered credentials, and gave hackers access to sensitive data.
Malware Incident: Hackers use infected devices to access corporate networks.
Equifax Breach: Exploited an Apache Struts vulnerability, affecting 147 million people due to a failure to patch known threats.
Lessons Learned
Staying vigilant and proactively securing systems is crucial:
Call to Action
This format makes your transcript easy to read and highlights critical points for your blog audience.
Book Your Free Consult & Assessment
Start your security journey with a real conversation—no forms, no sales scripts.
When you reach out, a cybersecurity expert will work with you to truly understand your business or personal security needs.
We listen first and answer your questions, making sure Always-On Guard is a fit for you (not the other way around).
No credit card required. No pressure. Just practical guidance.
Step 1: Free Consultation
Call (972) 777-5572 or click the button below...
Enjoy a real, live conversation with our team—
tailored to your specific situation.
Step 2: Personalized Assessment
If you’re a match, we’ll walk you through a quick, 10-question assessment to pinpoint your cybersecurity needs. This isn’t a generic web form—it’s a guided, expert process.
Step 3: Free 14-Day Trial Onboarding
Once you complete your assessment, our team will schedule and guide your risk-free 14-day onboarding trial—so you can experience full protection, with zero commitment.
Call +1 866-943-5763 or click the button below...
LEARN MORE
MSP • vCISO • PARTNER INFORMATION
Fortifying Digital Frontiers: Your Bridge Over Cyber Breaches
© 2026 Cyber Secure Online LLC | All Rights Reserved